Running a private practice already demands enough from you. Adding hours of administrative work on...


Running a healthcare practice comes with great responsibility – especially when protecting patient information.
A HIPAA Security Risk Assessment helps identify potential risks before they become bigger problems, like data breaches or compliance violations that could lead to hefty fines.
While it might seem manageable to handle security checks in-house, it’s easy to overlook weak spots. That’s why many healthcare providers bring in third-party experts for a more thorough, objective assessment.
This step helps protect patient data and helps your practice meet compliance requirements.
A typical security risk assessment performs three functions:
Review existing security of protected health information
Identify threats and vulnerabilities
Assess risk for likelihood and impact
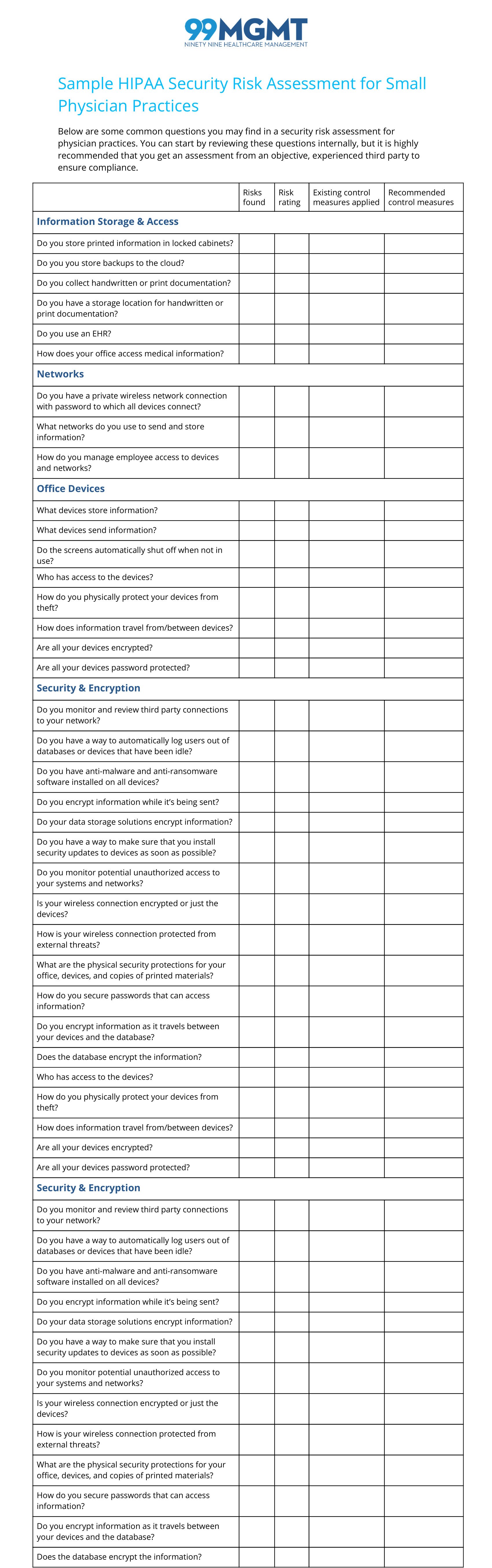
Upon completion, a typical security risk assessment report will provide recommendations for mitigating security risk and monitoring results. Your report will include the following items for review:
Questions you were asked in the assessment
Risks found, expressed as “TVS” or “Threat Vulnerability Statements”
Risk rating of each threat, often defined as “Low”, “Medium”, or “High”
Existing control measures applied (answers to the questions that were asked)
Recommended control measures (RCM), pre-designated by the ONC
Once you have the report, the next step is implementing the recommendations. This might mean updating security policies, strengthening protections, or training staff to handle risks more effectively.
HIPAA requires security risk assessments. Regular assessments help maintain compliance with safeguards that protect patient information. HIPAA recommends conducting these assessments at least once a year or when you make significant changes to systems, policies, or technology.
Vulnerabilities can lead to breaches of sensitive information, which have the following repercussions listed by HIPAA:
Settlements
Fines ranging anywhere from $100 - $50,000 per violation or per medical record
Criminal penalties including imprisonment (depending on the nature of the violation)
Exclusion from Medicare
The severity of these penalties depends on the level of negligence. Unintentional violations typically result in lower fines, while repeated or willful violations can lead to the highest penalties and legal action.
Note: It’s crucial to address identified issues ASAP, especially if you participate in the MACRA programs (MIPS & APMs). During an audit, your most recent security risk assessment will be one of the first things they’ll ask for.
Risks come from insecure processes, people, or technology. Here are some basic steps you can take to ensure compliance:
DOCUMENT any and all steps you take to manage risks
You have 90 days to either verify or provide this training to new employees
24/7 monitoring over your local IT infrastructure
Consider remote monitoring and management of IT to catch problems ASAP
Operate your network as a simple workgroup environment rather than domain based network
If you work with a risk assessment expert, you’ll receive personalized recommendations based on your full assessment.
A security risk assessment helps uncover vulnerabilities that could put patient information at risk. While reviewing risks internally is a good first step, a more detailed assessment provides a clearer picture of potential security gaps.
Below are some common questions in a security risk assessment for physician practices. You can start by reviewing these questions internally, but it is highly recommended that you get an assessment from an objective, experienced third party to maintain compliance.
A HIPAA Security Risk Assessment is more than just checking a compliance box – it’s about keeping patient information safe and maintaining trust in your practice. Addressing risks early helps prevent costly problems.
Regular assessments strengthen security measures and support compliance with HIPAA regulations. Bringing in a third-party expert can provide a thorough review, helping to catch issues that might otherwise go unnoticed. Prioritizing security protects both patient data and the long-term stability of your practice.
Starting a medical practice in Texas comes with many challenges, but the right resources can make the process smoother.


Running a private practice already demands enough from you. Adding hours of administrative work on...

Running a medical practice involves managing dozens of ongoing costs, and understanding them is...

A Texas physician opened a new practice with everything in place – staff hired, patients scheduled,...

Your biller is three weeks behind on claims. Two no-shows went unfilled this morning. Your office...

Every minute spent chasing paperwork or fixing scheduling issues is time taken away from patients....

Most physicians didn’t go through years of training to become billing experts, HR managers, or IT...

If your medical practice overhead seems to be eating into your revenue, you’re not alone. Research...
Marketing and referral strategies are part of running a private practice. In Texas, they come with...
.jpeg?height=200&name=alone-bills-calculator-1253591%20(1).jpeg)
Opening a medical clinic is rewarding – but it comes with upfront costs. Lease deposits. Equipment....

Ending a relationship with a patient isn’t something providers take lightly. But when certain...
Leave a Comment